 Australia’s National Cyber Security Deputy Secretary, Alastair MacGibbon, has today publicly named and shamed Xi Jinping’s Communist Party of China for ordering the hacking of “tens of thousands” of Australian technology companies.
Australia’s National Cyber Security Deputy Secretary, Alastair MacGibbon, has today publicly named and shamed Xi Jinping’s Communist Party of China for ordering the hacking of “tens of thousands” of Australian technology companies.
MacGibbon confirms that leading digital companies and managed service providers (MSPs) across all sectors of corporate Australia have been majorly hacked by Chinese state-backed hackers, stealing intellectual property and accessing customer profiles and transaction details, while masking their access as legitimate activity.
MacGibbon states:
“It’s the biggest and most audacious campaign I’ve seen. This is massive in its scope and its scale. It’s breathtaking.”
Think Telstra, Optus, TPG, ASIO, the ADF, AFP, government departments (energy, roads, water, health), Australia’s major banks, insurers, the Stock Exchange, Medicare, My Health Record, Centrelink, and digital firms in Australia – Microsoft, Apple, AgriDigital, hipages, Autodesk Australia, SAS, InfoTrack, Ansarada, Adobe, NetApp Australia, Atlassian, Salesforce, 4Mation Technologies, Canva, MYOB, Intuit Australia, DocuSign, AppDynamics, Houzz, Indeed, Airbnb, Cashrewards, Nuix Sydney, Accenture, plus every solar panel, wind turbine and drone in Australia.

China uses the cloud to step up spying on Australian business. MacGibbon verifies that serial Chinese theft continues to prey on and disadvantage Australian businesses and their staff.
“And that essentially takes food from the people of Australia. It helps them compete in a way that we can’t.”
America’s FBI Director Christopher Wray with Deputy Attorney General Rod Rosenstein has supported MacGibbon’s concerns, confirming that China’s intelligence services have hacked the world’s biggest providers of software services, including global tech giants like Hewlett Packard, SAP and IBM. Wray says it’s a most extraordinary penetration that has exposed major tech firms’ client companies commercial data running every aspect of Australian businesses, from human resources to accounts management.
And don’t use Alibaba.com – it’s Chinese with attitude.

In American today, US prosecutors have charged two Chinese nationals with computer hacking attacks on American government agencies and corporations, including major banking, healthcare, telecommunications, mining and manufacturing companies, the US space agency NASA, the US Navy and Department of Energy.
Zhu Hua and Zhang Shilong (their real names) use respective aliases ‘Godkiller‘ and ‘Atreexp‘.
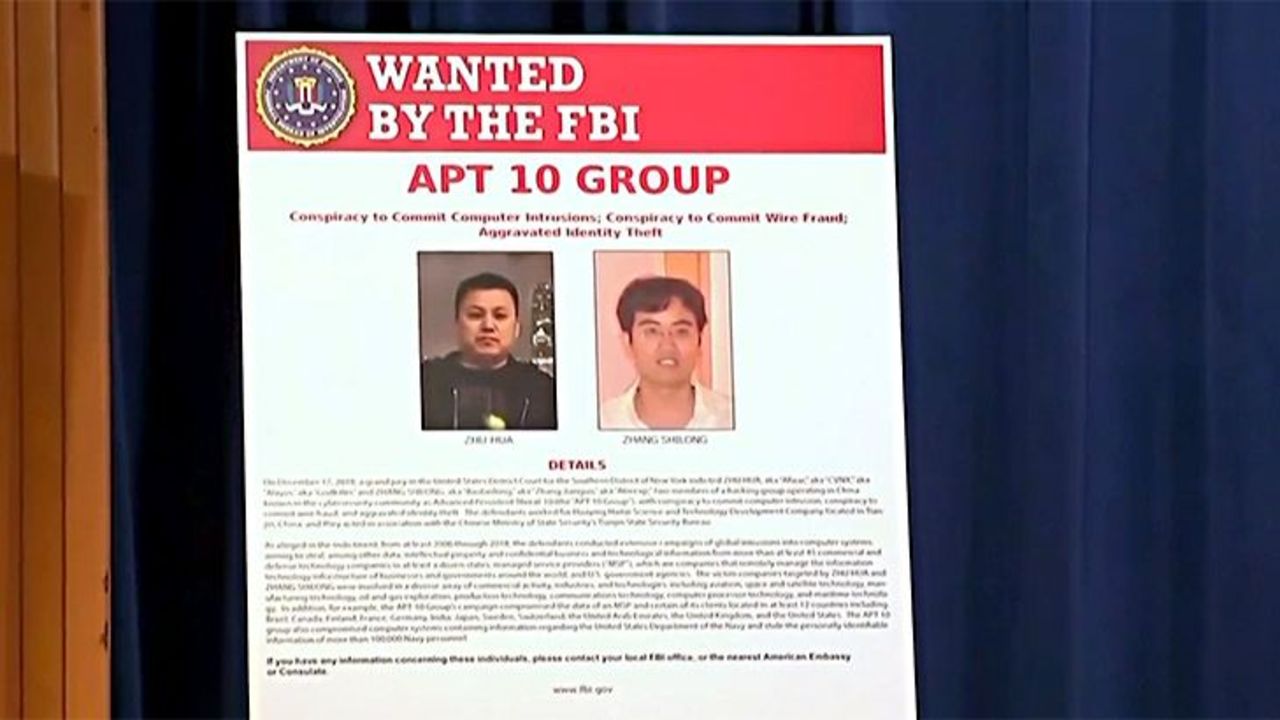
The two are directly linked to the Chinese Ministry of State Security’s group known as Advanced Persistent Threat 10 (APT10) that has been infiltrating computers systems since at least 2006. The group is also known as “Stone Panda,” “Red Apollo,” “MenuPass” and “POTASSIUM.”
The two are charged over industrial-scale theft of intellectual property and personal data from businesses and government agencies to secure competitive advantages for China.

FBI Director Christopher Wray said China had committed brazen, persistent theft and needed to be held accountable.
Wray:
“This is potentially the biggest hack the West has ever seen. There is still a lot we don’t know about the scale of the compromise because of the sophistication of the hack. But if you are a Western MSP you are likely to be caught up. No country poses a broader, more severe, and long-term threat to our nation’s economy and cyber infrastructure than China. China’s goal, simply put, is to replace the US as the world’s leading superpower, and they’re using illegal methods to get there.”
Both Zhu and Zhang (sounds like ‘Cheech and Chong’) have worked for a company called Huaying Huatai Science and Technology Development company in the northern Chinese city of Tianjin. Both are also linked with the ministry of state security in Tianjin. Zhu, known by aliases such as “Afwa,” “CVNX,” “Alayos,” and “Godkiller,” was responsible for registering malware domains and hacking infrastructure, as well as recruiting members for APT10.
Zhang, whose alternative names include “baobeiling,” “Zhang Jianguo” and “Atreexp”, registered domains and infrastructure as well as tested and developed malware used by the group. Beginning in or about 2006, the group breached the computers of more than 45 commercial and defence technology companies in aviation, space and satellite technology, pharmaceutical technology, and others in 12 US states, stealing “hundreds of gigabytes of sensitive data,” according to US prosecutors.
In 2014, Zhu and Zhang and other members of the group gained access to the managed service providers, companies that store client data remotely, of businesses and governments in at least 12 countries, including the US, the UK, Canada, Japan, Brazil, France, Finland, Sweden, Switzerland and the United Arab Emirates, Germany, and India. They also obtained the personal data of more than 100,000 personnel working for the US Navy. The two hackers sent customised emails with malware hidden in attachments related to the recipient. Once opened, the attachment would install malware, including one known as “Poison Ivy” used to steal usernames and passwords as users type them. The malware was also programmed to communicate with domains assigned to IP addresses of computers controlled by APT10.

Australia is pointing finger publicly at the Chinese government to rightly name and shame the celestials. Australia and intellectually advanced First World nations have long known this privately about China’s serial cyber theft culture. It’s just serial White envy.
Australia’s Foreign Minister Marise Payne and Home Affairs Peter Dutton have joined their counterparts in the United States and Britain to express “serious concern” over what they call a “global campaign of cyber-enabled commercial intellectual property theft” by the copy-cat culture.
The decision by governments in the US and Australia to effectively name and shame Beijing over the industrial espionage marks a major departure from the usual practice of not attributing hacking behaviour, and reflects the intense frustration of Canberra at China’s persistent efforts to steal commercial secrets.
China is the real concern in the cyber area, and the West is now calling them out. The jaundiced will want to continue stealing. We need to make it harder for the criminals
The only people who like Chinese are Chinese.
In totalitarian central Bejing, Dictator Xi’s Foreign Ministry has come out in frothing in neo-Commo denial, resolutely opposing such “slanderous” accusations criticising China for economic espionage, and urged Washington to withdraw its accusations.
That’s not likely under U.S. President Trump. He’s no time for celestial invaders and thieves of the West. The theft of intellectual property has formed a key part of his catch up trade war with cheap dumping China.

As far back as the 1850’s, our colonial nation suffered from illegal hordes of invading Chinese celestials who copied and contaminated Aussie Diggers on the 19th Century goldfields of the fair White colony.

“..heathen Mongolians” alright
Chinese even copied Special Fried Rice from Indonesian Nasi Goreng. No wonder other Asian nations are quick to tell ’em to piss off.
Canberra’s former PM Malcolm Turncoat with Premier Li Keqiang of China agreed not to steal commercial secrets. They can copy Turncoat and indeed welcome to take home the original.
Turncoat was never about Australia’s national interests, just his own globalist republican agenda from his palatial Point Piper digs funded by Goldman Sachs
Ya just can’t trust Chinese. They’re lurking in ya smart phone, in the cloud, even in ya smart fridge to see if there’s leftover special fried rice. No bloody wonder Huawei was rejected Australia’s national 5G network rollout gig. Every connection would have been tapped back to Beijing. No wonder Hong Kong’s CK Group was rejected from buying Australia’s energy network. Beijing would have flicked Australia’s power off.

Well the Chinese can copy KFC. They’re welcome to monkey food.